Network Requirements
- A PC acts as an FTP server, and Device acts as an FTP client. The network between the Device and the Client is normal.
- Set up the security data channel between FTP Server and FTP Client, providing the security guarantee for the data transmission.
- The file can be uploaded and downloaded between FTP Client and FTP Server.
Network Topology

Figure 4-9 Networking for configuring a device as an FTPS client
Configuration Steps
Step 1: Configure the IPv4 address of the interface (omitted).
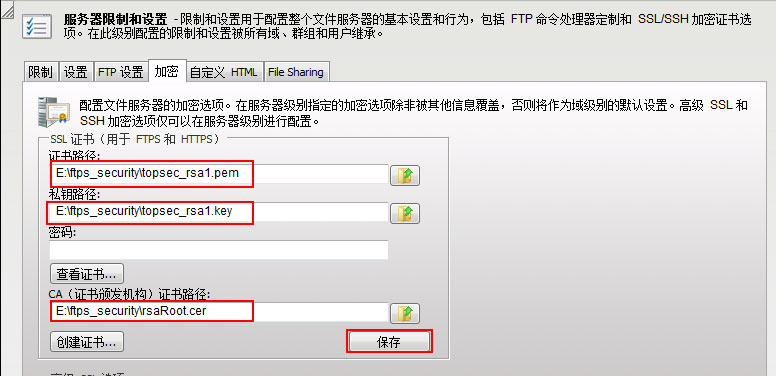
Step 2: Install the certificate at the FTP Server, and set the FTP user certificate path, private key path, and CA certificate path:
Step 3: FTP Client imports the FTP CA certificate, user certificate, and private key.
#Create one domain test on the device:
|
Device#configure terminal
Device(config)#crypto ca identity test
Device(ca-identity)#exit
|
#Bind FTP with the domain test:
| Device(config)#ip ftp secure-identity test |
#Open the CA certificate (rsaRoot.cer) by the notepad, copy the content, input crypto ca import certificate to test on the shell, and import the certificate to the device domain test according to the prompt:
|
Device(config)#crypto ca import certificate to test
% Input the certificate data, press <Enter> twice to finish:
-----BEGIN CERTIFICATE-----
MIIDBzCCAnCgAwIBAgIITpXH17Hj/AswDQYJKoZIhvcNAQEFBQAwYjELMAkGA1UE
BhMCQ04xEDAOBgNVBAgMB0JFSUpJTkcxDjAMBgNVBAoMBUNJRUNDMQ8wDQYDVQQL
DAZHRkEgQ0ExIDAeBgNVBAMMF01pbmlDQSBGcmVCU0QgUm9vdCBDZXJ0MB4XDTA5
MDgwMzA2MDY1MloXDTE5MDgwMzA2MDY1MlowYjELMAkGA1UEBhMCQ04xEDAOBgNV
BAgMB0JFSUpJTkcxDjAMBgNVBAoMBUNJRUNDMQ8wDQYDVQQLDAZHRkEgQ0ExIDAe
BgNVBAMMF01pbmlDQSBGcmVCU0QgUm9vdCBDZXJ0MIGeMA0GCSqGSIb3DQEBAQUA
A4GMADCBiAKBgHXZMtpxzH8p0uUt6QomUhuJNcy9iyYhoJVx4I3T6kpmx9cdzapM
RoKUa9eB/jCzhgctQc7ZDuKP+gafHWgZtbzwwSVksVsNmFqBivixveGx9dCrtequ
+vDiXVyDVPSNDDTmamMGYyCb0N7aSOzdgv6BYyQKyy/Y0FK6/v/v4NUxAgMBAAGj
gcYwgcMwPQYDVR0fBDYwNDAyoDCgLoYsaHR0cDovLzE2OC4xNjguMTcuNDY6OTAw
MC9nZmEvY3JsL2dmYWFwcC5jcmwwSAYDVR0gBEEwPzA9BggrBgEEAYcrMjAxMC8G
CCsGAQUFBwIBFiNodHRwOi8vd3d3LmdmYXBraS5jb20uY24vcG9saWN5LmRvYzAL
BgNVHQ8EBAMCAuQwDAYDVR0TBAUwAwEB/zAdBgNVHQ4EFgQUhnY8uZXbE2iX1mXO
ipvfuDUgAeswDQYJKoZIhvcNAQEFBQADgYEAcNPdTE+YpfOQn8lW1oF7TkGJ/Vzd
c0O5UUB+jPhYkj+fXUX8WyxabOxgl3u+7DJ/3gHw1rO8ZcDO94Wz+nBsile5tFv7
/bHz0yqJVoUJMIaWOdmLXJj5fI5GeBCprzLM88RJCv6LBHfg4ThOC4Ds80Ssive1
eAod+7kbmVPOZg8=
-----END CERTIFICATE-----
% Input the private key data, press <Enter> twice after data to finish or press <Enter> without data to ignore:
% The Root CA Certificate has the following attributes:
Serial Number: 4e95c7d7b1e3fc0b
Subject: C=CN, ST=BEIJING, O=CIECC, OU=GFA CA, CN=MiniCA FreBSD Root Cert
Issuer : C=CN, ST=BEIJING, O=CIECC, OU=GFA CA, CN=MiniCA FreBSD Root Cert
Validity
Start date: 2009-08-03 06:06:52
End date: 2019-08-03 06:06:52
Usage: General
Fingerprint(sm3) :18d39e4c50c9ad8b11446ac7ac1736f853ac92e769994b98233b48787562429c
Fingerprint(sha1):ab3559e26384539ffcac3c76b5a5e7a1f7073dfb
% Do you accept this root ca-certificate[yes]/[no]:
% Please answer 'yes' or 'no'.
% Do you accept this root ca-certificate[yes]/[no]:
Nov 11 2015 19:06:04: %PKI-CERTIFICATE_STATECHG-5: Certificate(issuer:C=CN, ST=BEIJING, O=CIECC, OU=GFA CA, CN=MiniCA FreBSD Root Cert, sn:4E95C7D7B1E3FC0B, subject:C=CN, ST=BEIJING, O=CIECC, OU=GFA CA, CN=MiniCA FreBSD Root Cert) state valid
% PKI: Import Certificate success.
|
#Open the user certificate (topsec_rsa2_myself.pem) and the private key certificate (topsec_rsa2_myself.key) by the notepad, copy the content, input the command crypto ca import certificate to test on the shell, and import the certificates to the device domain test according to the prompt in turn:
|
Device(config)#crypto ca import certificate to test
% Input the certificate data, press <Enter> twice to finish:
-----BEGIN CERTIFICATE-----
MIIDVTCCAr6gAwIBAgIQEJ7twbl3pDlzJz99DFOKOzANBgkqhkiG9w0BAQUFADBiMQswCQYDVQQGEwJDTjEQMA4GA1UECAwHQkVJSklORzEOMAwGA1UECgwFQ0lFQ0MxDzANBgNVBAsMBkdGQSBDQTEgMB4GA1UEAwwXTWluaUNBIEZyZUJTRCBSb290IENlcnQwHhcNMTIwNjI2MDUwMTIzWhcNMzIwNjI2MDUwMTIzWjB/MQswCQYDVQQGEwJDTjEQMA4GA1UECAwHYmVpamluZzESMBAGA1UEBwwJZG9uZ2NoZW5nMQ4wDAYDVQQKDAVjaWVjYzEMMAoGA1UECwwDZ2ZhMR0wGwYJKoZIhvcNAQkBFg50ZXN0QGVjLmNvbS5jbjENMAsGA1UEAwwEcnNhMjCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA6AlNqTnNsV9Yyij2tTMppB9C5VCLtkPh9KlIq/ZTlVhrJED+N5HVfQQyZYS/z4JWAip50dyP1+NP+bvP+pb9CfEaJ8+ObYQnfUH6qiPccLkWO3XYanu6Dw5EMJYntwglSKmk1Pcc+j+yzWnwYMDFcbSsQ+8J5UzlesFhU7GnXacCAwEAAaOB7jCB6zA+BgNVHR8ENzA1MDOgMaAvhi1odHRwczovLzIxMS44OC4yNS4xODo4NDQ0L2dmYS9jcmwvUlNBMTAyNC5jcmwwUQYDVR0gBEowSDBGBggrBgEEAYcrMjA6MDgGCCsGAQUFBwIBFixodHRwczovLzIxMS44OC4yNS4xODo4NDQ0L2dmYS9jcmwvUlNBMTAyNC5wbDALBgNVHQ8EBAMCA/gwCQYDVR0TBAIwADAdBgNVHQ4EFgQUp/9/ODGLR84syxPaBkLG3mCpU5YwHwYDVR0jBBgwFoAUhnY8uZXbE2iX1mXOipvfuDUgAeswDQYJKoZIhvcNAQEFBQADgYEAYrFZQrINHoLN9odcGctzTRGVmMcv9sJ0ncgUEfbrLu6QUodQy3jjxWFIxheJK1btfF66/ShuKtZpqJ1WE9l92tfIHwLpXT0gujtxNi02TOPBNEU7P9nUgxgfDG+uhyPTeufSkfn3LCTHmGfVORF2soGSlaUPV1Zy5E9hmFZoMhs=-----END CERTIFICATE-----
% Input the private key data, press <Enter> twice after data to finish or press <Enter> without data to ignore:
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQDoCU2pOc2xX1jKKPa1MymkH0LlUIu2Q+H0qUir9lOVWGskQP43kdV9BDJlhL/PglYCKnnR3I/X40/5u8/6lv0J8Ronz45thCd9QfqqI9xwuRY7ddhqe7oPDkQwlie3CCVIqaTU9xz6P7LNafBgwMVxtKxD7wnlTOV6wWFTsaddpwIDAQABAoGBAMnJNWliJFgI4+1CvHGN4buhmApWBnnmBL1A7jrlh4CMGPi5MJrgzvjeSnlwfWIXJXbSu4feuJT1UFqMkuyIm9l+k8Rm3hjClXIlfNV/ykG6a6GIVFYGxQWhaL50Pm6S7xXL9Ryd6hnOHUUtwuLvkpBTx/4qvrIABDtXRjVglvApAkEA9BN1ZxM31BOyeB6KXvvmXD6/+dGaDfE4Dbcijy1LgKliaEBJ00e/0R9ekg6myGTU2asJvPtkaXPqcwvU6+e2mwJBAPNfRTk9LzUlNmTV2DrsE9k3rbPnqqS9wb/mLUNdv2FQeoY/Zf4qh0WXsug2q/6GPsvLUA7mbdArGFUwwQbw3+UCQQC8r25LSOgX40JM6g8+bq4fEcOHdSoLLTeQIststC9yP3/75/cqhoUbPYz2jK0SriB+RWM53X46p4nPdo4b8P2RAkBGjoBLL+nXxooWgcjGjFrUxsedOLTIPhtFvz2wIiWx2NsswISZQ0skae58VB1ZFSJvguoa58M+bsAHMrNDh+HhAkBcNAjKBDdVw0ll6bNoRGugEvuo3Z3O0kbVcjzZld+4aVG4DzvEp1ZbsYRv9YPMtpnzmB7WZUshAL99nHnHxtbh-----END RSA PRIVATE KEY-----
Nov 11 2015 19:06:56: %PKI-CERTIFICATE_STATECHG-5: Certificate(issuer:C=CN, ST=BEIJING, O=CIECC, OU=GFA CA, CN=MiniCA FreBSD Root Cert, sn:109EEDC1B977A43973273F7D0C538A3B, subject:C=CN, ST=beijing, L=dongcheng, O=ciecc, OU=gfa, E=test@ec.com.cn, CN=rsa2) state valid
% PKI: Import Certificate success.
|
#After importing the certificate successfully, you can use the command show crypto ca certificates to view that the status is Valid.
|
Device#show crypto ca certificates
Root CA Certificate:
Status: Valid
Serial Number: 4e95c7d7b1e3fc0b
Subject: C=CN, ST=BEIJING, O=CIECC, OU=GFA CA, CN=MiniCA FreBSD Root Cert
Issuer : C=CN, ST=BEIJING, O=CIECC, OU=GFA CA, CN=MiniCA FreBSD Root Cert
Validity
Start date: 2009-08-03 06:06:52
End date: 2019-08-03 06:06:52
Key Type: RSA(1023 bit)
Usage: General
Fingerprint(sm3):18d39e4c50c9ad8b11446ac7ac1736f853ac92e769994b98233b48787562429c
Fingerprint(sha1):ab3559e26384539ffcac3c76b5a5e7a1f7073dfb
Associated Identity: test
index: 3
My Certificate:
Status: Valid
Serial Number: 109eedc1b977a43973273f7d0c538a3b
Subject: C=CN, ST=beijing, L=dongcheng, O=ciecc, OU=gfa, E=test@ec.com.cn, CN=rsa2
Issuer : C=CN, ST=BEIJING, O=CIECC, OU=GFA CA, CN=MiniCA FreBSD Root Cert
Validity
Start date: 2012-06-26 05:01:23
End date: 2032-06-26 05:01:23
Key Type: RSA(1024 bit)
Usage: General
Fingerprint(sm3):504599a2f170c51b62b2f8b0850f33a5595bc9e592d14eae9c90b1e59de35a89
Fingerprint(sha1):080614a82cc4f3786458c585f9a58edf19da19bd
Associated Identity: test
index: 4
|
Step 4: Upload and download the file between FTP Client and FTP Server.
#FTP Client uploads the file to the FTP Server.
|
Device#filesystem
Device1(config-fs)#copy file-system startup ftps 1.0.0.1 a a startup VerifyType peer
Copying!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Total 103440 bytes copying completed.
|
#FTP Client downloads the file from FTP Server.
|
Device(config-fs)#ftpscopy 1.0.0.1 a a test.doc test.doc VerifyType peer
Downloading########################################################################################################################################################################################################################################################################################### OK!
|
Step 5: Check the result.
#After downloading, view the downloaded file in the file system of Device.
Device(config-fs)#dir
size date time name
------------ ------ ------ --------
10189 NOV-04-2015 20:27:03 history
436578 NOV-04-2015 20:33:08 test.doc
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng




.png)

























