Network Requirements
- PC acts as the local terminal and installs the SecureCRT software.
- PC acts as the local terminal and can access Device via the SSH public key.
Network Topology

Figure 2‑11: Network topology of configuring a local device to log in to a remote device by the SSH public key authentication mode
Configuration Steps
Step 1: Configure the IP address of the interface and configure the routing protocol to make the PC and Device intercommunicate with each other (omitted).
Step 2: Configure the SSH service and FTP function.
|
Device#configure terminal
Device(config)#ip ssh server
|
Step 3: Configure the login user name of Device.
|
Device(config)#local-user user1 class manager
Device(config-user-manager-user1)#service-type ssh
Device(config-user-manager-user1)#exit
|
Step 4: On PC, generate the SSH public key file.
#The document takes Windows operation system as an example. SecureCRT uses Version 8.5. On PC, open the SecureCRT software tool bar and click the Tools button. In the drop-down menu, click Create Public Key (C) to display the wizard of generating the key, and click Next.
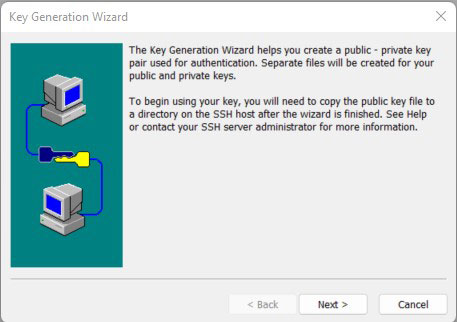
#Key type: Select any one from DSA and RSA. Here, take DSA as an example and click Next.
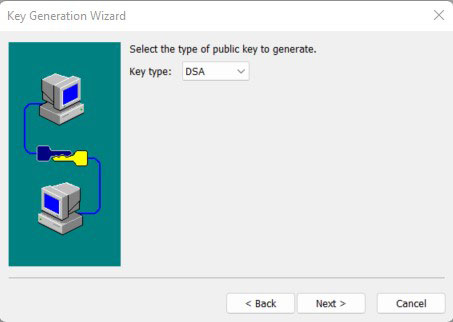
#The pass phrase is taking effect at the local and you can ignore. Click Next.
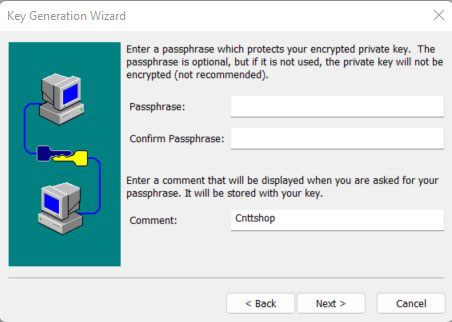
#Fill in the key length according to the description and click Next.
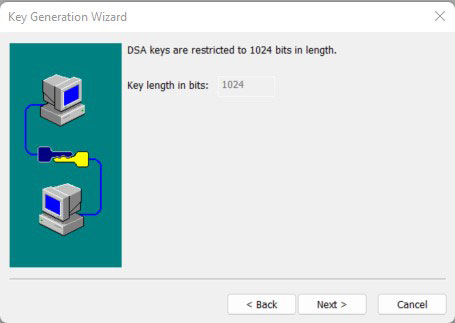
#To generate the key, you need to move the mouse continuously. After generating the key, click Next.
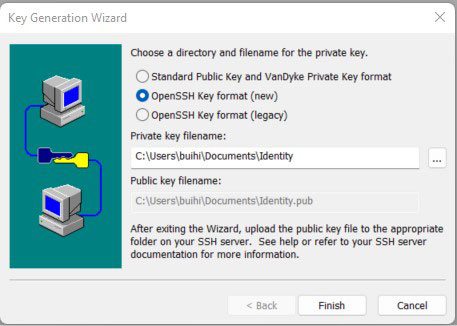
#Select the format of storing the key. Here, select the OpenSSH key format and click Finish.
#In the FTP server path of the PC, create the file “authorized_keys”, copy all content of the public key file “Identity.pub” to “authorized_keys”, and copy the file “authorized_keys” to /flash/sshpubkey/user1/.
|
Device#filesystem
Device(config-fs)#mkdir sshpubkey
Device(config-fs)#cd sshpubkey
Device(config-fs)#mkdir user1
Device(config-fs)#cd user1
Device(config-fs)#copy ftp 2.0.0.1 username password authorized_keys file-system authorized_keys
|

-
For the format of storing the key, select OpenSSH and the other formats are not supported.
- When copying the “Identity.pub” content, select all and then copy, and do not need to change a line.
- When multiple clients use one user to log in, change a line after the public key information stored by “authorized_keys”, then paste the information of another public key, and superimpose.
- By default, the device does not have the directory /flash/sshpubkey/user1/, and you need to create in filesystem. User1 in the directory is the user name used by authentication. The user name is the user on the device. If the user name is user2, create /flash/sshpubkey/user2/.
- SSH public key authentication does not support SSHv1.
Step 5: Check the result.
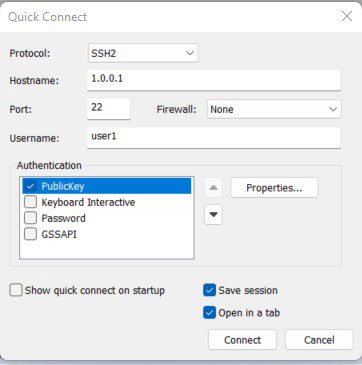
PC uses the SecureCRT software to set up the SSH connection, use publickey first or unique authentication, click Connect, and you can see that the connection is not required to input the password, but can log into the device directly.
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar![Module quang Inphi]() Module quang Inphi
Module quang Inphi![Module Quang Intel]() Module Quang Intel
Module Quang Intel![Module quang Finisar]() Module quang Finisar
Module quang Finisar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng







.png)































