Network Requirements
- Configure OSPF for all devices run OSPF, and configure area authentication for the devices. Configure simple text authentication for Area 0, and configure MD5 authentication for Area 1.
- Configure OSPF interface authentication, configure interface authentication of Area 0 to simple text authentication, and configure interface authentication of Area 1 to MD5 authentication.
- After configuration is completed, devices should able to normally set up neighbor relations and learn route from each other.
Network Topology
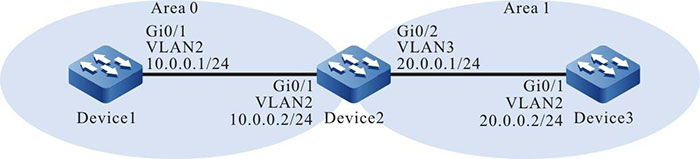
Figure 7-2 Networking for Configuring OSPF Authentication
Configuration Steps
Step 1: Create VLANs, and add ports to the required VLANs. (Omitted)
Step 2: Configure IP addresses for the ports. (Omitted)
Step 3: Configure an OSPF process, and configure the interfaces to cover different areas, and enable area authentication. Configure the simple text authentication for Area 0, and configure the MD5 authentication for Area 1.
#On Device1, configure an OSPF process and configure the area authentication function.
|
Device1#configure terminal
Device1(config)#router ospf 100
Device1(config-ospf)#router-id 1.1.1.1
Device1(config-ospf)#area 0 authentication
Device1(config-ospf)#network 10.0.0.0 0.0.0.255 area 0
Device1(config-ospf)#exit
|
#On Device2, configure an OSPF process and configure the area authentication function.
Device2#configure terminal
Device2(config)#router ospf 100
Device2(config-ospf)#router-id 2.2.2.2
Device2(config-ospf)#area 0 authentication
Device2(config-ospf)#area 1 authentication message-digest
Device2(config-ospf)#network 10.0.0.0 0.0.0.255 area 0
Device2(config-ospf)#network 20.0.0.0 0.0.0.255 area 1
Device2(config-ospf)#exit |
#On Device3, configure an OSPF process and configure the area authentication function.
|
Device3#configure terminal
Device3(config)#router ospf 100
Device3(config-ospf)#router-id 3.3.3.3
Device3(config-ospf)#area 1 authentication message-digest
Device3(config-ospf)#network 20.0.0.0 0.0.0.255 area 1
Device3(config-ospf)#exit
|
#Query the OSPF process information of Device1.
Device1#show ip ospf 100
Routing Process "ospf 100" with ID 1.1.1.1
Process bound to VRF default
Process uptime is 30 minutes
IETF NSF restarter support disabled
IETF NSF helper support enabled
Conforms to RFC2328, and RFC1583 Compatibility flag is disabled
Supports only single TOS(TOS0) routes
Supports opaque LSA
Supports Graceful Restart
Initial SPF schedule delay 5000 msecs
Minimum hold time between two consecutive SPFs 10000 msecs
Maximum wait time between two consecutive SPFs 10000 msecs
Refresh timer 10 secs
Number of external LSA 0. Checksum Sum 0x000000
Number of opaque AS LSA 0. Checksum Sum 0x000000
Number of non-default external LSA is 0
External LSA database is unlimited.
Not Support Demand Circuit lsa number is 0, autonomy system support flood DoNotAge Lsa
Number of areas attached to this router: 1
Area 0 (BACKBONE) Number of interfaces in this area is 1(1)
Number of fully adjacent neighbors in this area is 1
Number of fully adjacent sham-link neighbors in this area is 0
Area has simple password authentication
SPF algorithm last executed 00:27:43.916 ago
SPF algorithm executed 3 times
Number of LSA 4. Checksum Sum 0x0160f7
Not Support Demand Circuit lsa number is 0,
Indication lsa (by other routers) number is: 0,
Area support flood DoNotAge Lsa
According to the queried information, the area authentication is the simple text mode.
#Query the OSPF neighbors and routing table of Device1.
Device1#show ip ospf neighbor
OSPF process 100:
Neighbor ID Pri State Dead Time Address Interface
2.2.2.2 1 Full/DR 00:00:38 10.0.0.2 vlan2
Device1#show ip route
Codes: C - connected, S - static, R - RIP, O - OSPF, OE-OSPF External, M Management
D - Redirect, E - IRMP, EX - IRMP external, o - SNSP, B BGP, i-ISIS
Gateway of last resort is not set
C 10.0.0.0/24 is directly connected, 00:14:01, vlan2
O 20.0.0.0/24 [110/2] via 10.0.0.2, 00:10:38, vlan2
C 127.0.0.0/8 is directly connected, 20:55:08, lo0
On Device1, neighbors can be normally set up, and routes can be learnt normally.
#Query the OSPF process information of Device3.
Device3#show ip ospf 100
Routing Process "ospf 100" with ID 3.3.3.3
Process bound to VRF default
Process uptime is 28 minutes
IETF NSF restarter support disabled
IETF NSF helper support enabled
Conforms to RFC2328, and RFC1583Compatibility flag is disabled
Supports only single TOS(TOS0) routes
Supports opaque LSA
Supports Graceful Restart
Initial SPF schedule delay 5000 msecs
Minimum hold time between two consecutive SPFs 10000 msecs
Maximum wait time between two consecutive SPFs 10000 msecs
Refresh timer 10 secs
Number of external LSA 0. Checksum Sum 0x000000
Number of opaque AS LSA 0. Checksum Sum 0x000000
Number of non-default external LSA is 0
External LSA database is unlimited.
Not Support Demand Circuit lsa number is 0, autonomy system support flood DoNotAge Lsa
Number of areas attached to this router: 1
Area 1 Number of interfaces in this area is 1(1)
Number of fully adjacent neighbors in this area is 1
Number of fully adjacent sham-link neighbors in this area is 0
Number of fully adjacent virtual neighbors through this area is 0
Area has message digest authentication
SPF algorithm last executed 00:24:01.783 ago
SPF algorithm executed 5 times
Number of LSA 4. Checksum Sum 0x0337cf
Not Support Demand Circuit lsa number is 0,
Indication lsa (by other routers) number is: 0,
Area support flood DoNotAge Lsa
According to the queried information, the area authentication is the MD5 authentication mode.
#Query the OSPF neighbors and routing table of Device3.
Device3#show ip ospf neighbor OSPF process 100:
Neighbor ID Pri State Dead Time Address Interface
2.2.2.2 1 Full/Backup 00:00:33 20.0.0.1 vlan2
Device3#show ip route
Codes: C - connected, S - static, R - RIP, O - OSPF, OE-OSPF External, M Management
D - Redirect, E - IRMP, EX - IRMP external, o - SNSP, B BGP, i-ISIS
Gateway of last resort is not set
O 10.0.0.0/24 [110/2] via 20.0.0.1, 00:09:31, vlan2
C 20.0.0.0/24 is directly connected, 00:20:36, vlan2
C 127.0.0.0/8 is directly connected, 24:00:06, lo0
On Device3, neighbors can be normally set up, and routes can be learnt normally.
Step 4: Configure OSPF interface authentication.
#On Device1, configure interface VLAN2 with simple text authentication, and set the password to admin.
|
Device1(config)#interface vlan2
Device1(config-if-vlan2)#ip ospf authentication
Device1(config-if-vlan2)#ip ospf authentication-key 0 admin
Device1(config-if-vlan2)#exit
|
#On Device2, configure interface VLAN2 with simple text authentication, and set the password to admin. Configure interface VLAN3 with MD5 authentication, set Key ID to 1, and set password to admin.
|
Device2(config)#interface vlan2
Device2(config-if-vlan2)#ip ospf authentication
Device2(config-if-vlan2)#ip ospf authentication-key 0 admin
Device2(config-if-vlan2)#exit
Device2(config)#interface vlan3
Device2(config-if-vlan3)#ip ospf authentication message-digest
Device2(config-if-vlan3)#ip ospf message-digest-key 1 md5 0 admin
Device2(config-if-vlan3)#exit
|
#On Device3, configure interface VLAN2 with MD5 authentication, set Key ID to 1, and set password to admin.
|
Device3(config)#interface vlan2
Device3(config-if-vlan2)#ip ospf authentication message-digest
Device3(config-if-vlan2)#ip ospf message-digest-key 1 md5 0 admin
Device3(config-if-vlan2)#exit
|
Step 5: Check the result.
#Query the OSPF neighbor information of Device2.
Device2#show ip ospf neighbor OSPF process 100:
Neighbor ID Pri State Dead Time Address Interface
1.1.1.1 1 Full/Backup 00:00:33 10.0.0.1 vlan2
3.3.3.3 1 Full/DR 00:00:39 20.0.0.2 vlan3
#Query the OSPF interface information of Device2.
Device2#show ip ospf interface vlan2
vlan2 is up, line protocol is up
Internet Address 10.0.0.2, 10.0.0.255( a[10.0.0.2] d[10.0.0.255]) Area 0, MTU 1500
Process ID 100, Router ID 2.2.2.2, Network Type BROADCAST, Cost: 1
Transmit Delay is 1 sec, State DR, Priority 1, TE Metric 0
Designated Router (ID) 2.2.2.2, Interface Address 10.0.0.2
Backup Designated Router (ID) 1.1.1.1, Interface Address 10.0.0.1
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
Hello due in 00:00:04
Neighbor Count is 1, Adjacent neighbor count is 1
Crypt Sequence Number is 0
Graceful restart proxy id is 0x0
Hello received 406 sent 454, DD received 8 sent 6
LS-Req received 2 sent 2, LS-Upd received 11(LSA: 15) sent 10(LSA: 14)
LS-Ack received 10 sent 0, Discarded 0
Device2#show ip ospf interface vlan3
vlan3 is up, line protocol is up
Internet Address 20.0.0.1, 20.0.0.255( a[20.0.0.1] d[20.0.0.255]) Area 1, MTU 1500
Process ID 100, Router ID 2.2.2.2, Network Type BROADCAST, Cost: 1
Transmit Delay is 1 sec, State Backup, Priority 1, TE Metric 0
Designated Router (ID) 3.3.3.3, Interface Address 20.0.0.2
Backup Designated Router (ID) 2.2.2.2, Interface Address 20.0.0.1
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
Hello due in 00:00:00
Neighbor Count is 1, Adjacent neighbor count is 1
Crypt Sequence Number is 485
Graceful restart proxy id is 0x0
Hello received 412 sent 454, DD received 9 sent 12
LS-Req received 3 sent 3, LS-Upd received 9(LSA: 10) sent 13(LSA: 16)
LS-Ack received 13 sent 8, Discarded 0
After MD5 authentication is configured, a Crypt Sequence Number is generated. In the case of simple text authentication, no sequence number is generated.

-
In configuring OSPF authentication, you can configure only area authentication or interface authentication, or configure both of them.
- If both area authentication and interface authentication are configured, interface authentication takes effect first.
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar![Module quang Inphi]() Module quang Inphi
Module quang Inphi![Module Quang Intel]() Module Quang Intel
Module Quang Intel![Module quang Finisar]() Module quang Finisar
Module quang Finisar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng







.png)
























