Network Requirements
- PC1 and PC2 serve as the local terminals, and can log into Device via telnet, ssh.
- Device can limit the login for PC1 and PC2 via the user and IP.
Network Topology
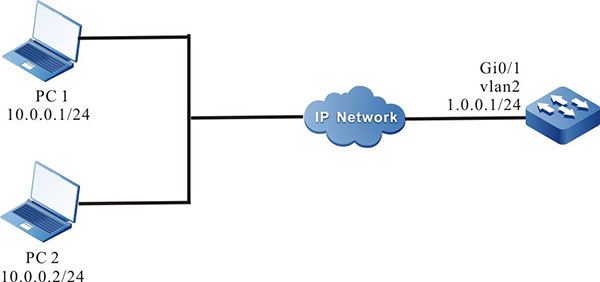
Figure 7‑1 Networking for configuring the login limit based on the user, IP
Configuration Steps
Step 1: Configure the IP address of the interface, and configure the routing protocol to make PC1, PC2, and Device communicate with each other (omitted).
Step 2: Configure the login limit function based on the user, IP.
#Enable the telnet, ssh login security function.
|
Device#configure terminal
Device(config)#service login-secure telnet
Device(config)#service login-secure ssh
|
#Configure the maximum try times of the telnet and ssh IP as 5 respectively, and the maximum try times of the user is 5.
|
Device(config)#login-secure telnet ip-addr max-try-time 5
Device(config)#login-secure telnet user max-try-time 5
Device(config)#login-secure ssh ip-addr max-try-time 5
Device(config)#login-secure ssh user max-try-time 5
|
Step 3: Enable the ssh service of Device, configure the user name and password, and set using the local authentication login.
|
Device(config)#ip ssh server
Device(config)#local-user user1 class manager
Device(config-user-manager-user1)#service-type ssh
Device(config-user-manager-user1)#password 0 admin
Device(config-user-manager-user1)#exit
Device(config)#line vty 0 15
Device(config-line)#login aaa
Device(config-line)#exit
|
Step 4: Check the result.
#PC1 tries to login to Device via telnet, and the user name is user1. After inputting the wrong password for successive 6 times, view the user information of the telnet login security statistics on Device:
Device#show login-secure telnet user
telnet module forbidden user information:
user try-time forbid-time wd-id number record-time
--------- -------- ----------- ------ ------ -----------
user1 6 00:09:00 0x167f9c20 0 00:01:00
You can see that user1 is regarded as the login attack user, and cannot log into the device via telnet within10 minutes.
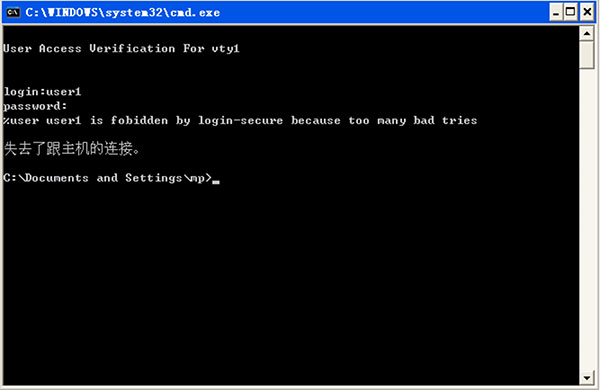
Here, PC1 tries to use user1 to log into Device via telnet again, and the system prompts the login is prohibited.
#PC2 tries to log into Device via ssh, and uses the un-configured user name of Device. After logging in for successive 6 times, view the ip information of the ssh login security statistics:
Device#show login-secure ssh ip-addr
ssh module forbidden login address:
client address try-time forbid-time wd-id type number record-time
-------------- -------- ----------- ------ ------ ------ -----------
10.0.0.2 6 00:09:00 0x167f9c80 login 0 00:01:00
You can see that IP address of PC2 is regarded as the login attack user, and cannot log into the device via ssh within10 minutes.
Here, PC1 tries to log into Device via ssh again, and the system prompts the login is prohibited.

-
It is regarded as the login attack and is prohibited only after the login times exceeds the configured maximum retry times. When the login times is equal to the configured maximum times, it is not prohibited.
- Some ssh clients on the PC will retry inside after logging fails. In this case, the device is still recorded as multiple logins.
- By default, the device enables the telnetm ssh login security function.
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng




.png)

























