Network Requirements
- There is authentication server (AAA Server), video server and one terminal device (PC) in the network.
- Configure the WDRR function. When the traffic of the egress port is congested, realize that the terminal traffic, video traffic and authentication traffic pass by some specified proportion.
Network Topology
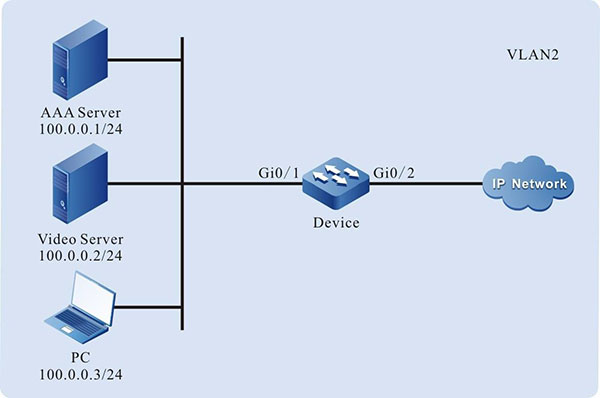
Figure 1-9 Networking of configuring the WDRR
Configuration Steps
Step 1: Configure the link type of the VLAN and port on Device.
#Create VLAN2.
|
Device#configure terminal
Device(config)#vlan 2
Device(config-vlan2)#exit
|
#Configure the link type of port gigabitethernet0/1 as Access and permit the services of VLAN2 to pass.
|
Device(config)#interface gigabitethernet 0/1
Device(config-if-gigabitethernet0/1)#switchport mode access
Device(config-if-gigabitethernet0/1)#switchport access vlan 2
|
#Configure the link type of port gigabitethernet0/2 as Trunk and permit the services of VLAN2 to pass.
|
Device(config-if-gigabitethernet0/1)#interface gigabitethernet 0/2
Device(config-if-gigabitethernet0/2)#switchport mode trunk
Device(config-if-gigabitethernet0/2)#switchport trunk allowed vlan add 2
Device(config-if-gigabitethernet0/2)#exit
|
Step 2: Configure the L3 action group.
#Configure the L3 action group named LP7 and the action is to remark the packet to queue 7.
|
Device(config)#l3-action-group LP7
Device(config-action-group)#remark l2-priority 1p 7
Device(config-action-group)#exit
|
#Configure the L3 action group named LP6 and the action is to remark the packet to queue 6.
|
Device(config)#l3-action-group LP6
Device(config-action-group)#remark l2-priority 1p 6
Device(config-action-group)#exit
|
#Configure the L3 action group named LP5 and the action is to remark the packet to queue 5.
|
Device(config)#l3-action-group LP5
Device(config-action-group)#remark l2-priority 1p 5
Device(config-action-group)#exit
|
Step 3: Configure the IP standard ACL.
#Configure the IP standard ACL with serial number 1 on Device.
|
Device(config)#ip access-list standard 1
|
#Configure binding the rule with the L3 action group named LP7, realizing that the authentication traffic packets are remarked to queue 7.
|
Device(config-std-nacl)#permit host 100.0.0.1 l3-action-group LP7
|
#Configure binding the rule with the L3 action group named LP6, realizing that the authentication traffic packets are remarked to queue 6.
|
Device(config-std-nacl)#permit host 100.0.0.2 l3-action-group LP6
|
#Configure binding the rule with the L3 action group named LP5, realizing that the authentication traffic packets are remarked to queue 5.
|
Device(config-std-nacl)#permit host 100.0.0.3 l3-action-group LP5
Device(config-std-nacl)#commit
Device(config-std-nacl)#exit
|
Step 4: Configure applying the IP standard ACL.
#Apply the IP standard ACL with serial number 1 to the ingress direction of port gigabitethernet0/1 on Device.
|
Device(config)#interface gigabitethernet 0/1
Device(config-if-gigabitethernet0/1)#ip access-group 1 in
Device(config-if-gigabitethernet0/1)#exit
|
#View the information of the ACL applied to the port on Device.
Device#show acl-object interface
-----------Interface-----Bind-----Instance
Interface----------------Direction----AclType---AclName
gi0/1 IN IP 1
Step 5: Configure the WDRR function.
#Configure the WDRR function on port gigabitethernet0/2, scheduling the packets of queue 5, queue 6 and queue 7 by the proportion of 1:2:3.
|
Device(config)#interface gigabitethernet 0/2
Device(config-if-gigabitethernet0/2)#queue-schedule wdrr 1 1 1 1 1 1 2 3
Device(config-if-gigabitethernet0/2)#exit
|
Step 6: Check the result.
#When the traffic of the egress port gigabitethernet0/2 is congested and the packet bytes are consistent, the terminal traffic, video traffic and authentication traffic pass by the proportion of 1:2:3; when the packet bytes are not consistent, the terminal traffic, video traffic and authentication traffic pass by the proportion of (1*the bytes of the authentication packet): (2*the bytes of the video bytes):(3*the bytes of the terminal packet).
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar![Module quang Inphi]() Module quang Inphi
Module quang Inphi![Module Quang Intel]() Module Quang Intel
Module Quang Intel![Module quang Finisar]() Module quang Finisar
Module quang Finisar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng







.png)
























