Overview Trusted Device Access
To protect the core network from being illegally accessed, the edge device of the core network must have high security. This requires that other network devices connected to the edge device of the core network must be a clear trusted device. The trusted device access function is based on a mature 802.1X protocol to prevent unauthorized devices from accessing the core network. The basic network topology, as shown in Figure 7-1, includes three entities: the Access Device, the Authentication System, and the Authentication Server System.
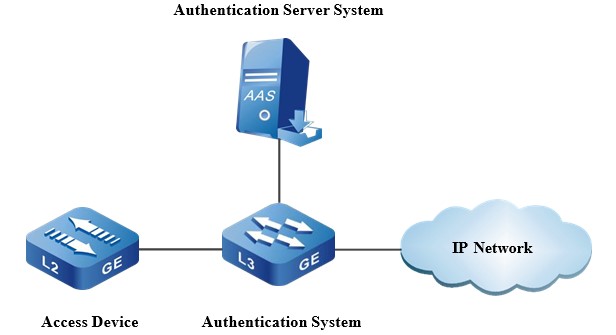
Figure 14-1 The access topology diagram of the trusted device
The specific method of the trusted device access is as follows:
- Enable the access function of the trusted device on the access device, and configure the required identity credentials and related parameters on the access device and authentication server.
- Enable the 802.1X device authentication function on the authentication device, the port connected to the access device becomes the controlled port waiting for the access of the access device.
- The access device automatically initiates the 802.1X authentication after connecting the authentication device. After passing the 802.1X authentication, the authentication device opens the controlled port, and the access device is connected to the network successfully.
- The access device regularly performs the keepalive authentication for the authentication device by the set the keepalive period of the authentication device.
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar![Module quang Inphi]() Module quang Inphi
Module quang Inphi![Module Quang Intel]() Module Quang Intel
Module Quang Intel![Module quang Finisar]() Module quang Finisar
Module quang Finisar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng







.png)
























