Network Requirements
- User PC1 and PC2 on the same VLAN access the IP network through Device. Enable the secure channel access control on Device.
- Authentication adopts the RADIUS authentication.
- PC1 is allowed to visit Update Server before authentication success and is allowed to visit Update Server and IP Network after authentication success.
- PC2 is allowed to visit Update Server and IP Network without authentication.
Network Topology
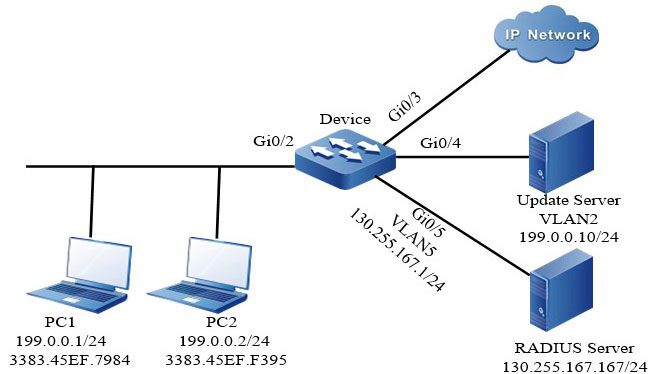
Figure 8–8 Networking of configuring secure channel
Configuration Steps
Step 1: Configure the link type of the VLAN and interface on the interface.
#Create VLAN2 and VLAN5 on Device.
|
Device#configure terminal
Device(config)#vlan 2,5
Device(config)#exit
|
#Configure the link type of interface gigabitethernet0/2 as Access, permitting services of VLAN2 to pass.
|
Device#configure terminal
Device(config)#interface gigabitethernet 0/2
Device(config-if-gigabitethernet0/2)# switchport mode access
Device(config-if-gigabitethernet0/2)# switchport access vlan 2
Device(config-if-gigabitethernet0/2)#end
|
#Configure link type of interface gigabitethernet 0/3–gigabitethernet 0/4 as Access on Device, permitting services of VLAN2 to pass. Configure the link type of interface gigabitethernet 0/5 as Access, permitting services of VLAN5 to pass. (Omitted)
Step 2: Configure the interface IP address of Device.
#Configure the IP address of VLAN5 as 130.255.167.1/24.
|
Device#configure terminal
Device(config)#interface vlan 5
Device(config-if-vlan5)#ip address 130.255.167.1 255.255.255.0
Device(config-if-vlan5)#end
|
Step 3: Configure AAA authentication.
#Enable AAA authentication on Device and adopt the RADIUS authentication mode. Configure the server key as admin, priority as 1, and IP address of RADIUS server as 130.255.167.167/24.
|
Device(config)#domain system
Device(config-isp-system)# aaa authentication dot1x radius-group radius
Device(config-isp-system)#exit
Device(config)#aaa server group radius radius
Device(config-sg-radius-radius)#server 130.255.167.167 priority 1 key admin
|
Step 4: Configure AAA server.
#Configure the user name, password, and key value on the AAA server as admin. (Omitted)
Step 5: Configure secure channel.
#Enable the secure channel access control on the interface gigabitethernet 0/2.
|
Device#configure terminal
Device(config)#interface gigabitethernet 0/2
Device(config-if-gigabitethernet0/2)#dot1x free-ip
Device(config-if-gigabitethernet0/2)#exit
|
#Configure a secure channel named channel and configure to allow PC1 to visit Update Server and configure to allow PC2 to visit Update Server and IP Network.
|
Device#configure terminal
Device(config)#hybrid access-list advanced channel
Device (config-adv-hybrid-nacl)#permit ip any any host 199.0.0.10 any
Device(config-adv-hybrid-nacl)#permit ip host 199.0.0.2 any any any
Device(config-adv-hybrid-nacl)#commit
|
#Apply the secure channel named channel.
|
Device#configure terminal
Device(config)#global security access-group channel
Device(config)#exit
|
Step 6: Check the result.
#View the secure channel configuration information.
|
Device#show dot1x free-ip 802.1X free-ip
Enable Interface (num:1): gi0/2
global security access-group channel
Total free-ip user number : 0
Device#show hybrid access-list channel
hybrid access-list advanced channel
10 permit ip any any host 199.0.0.10 any
20 permit ip host 199.0.0.2 any any any
|
It can be viewed that the secure channel is enabled on the interface gigabitethernet 0/2 and the interface is bound to the channel secure channel rule.
#PC1 can visit the Update Server and cannot visit other network resources before the authentication success.
#View the user authentication information after user PC1 initiates the authentication and authentication succeeds.
Device#show dot1x user
------------------------------------------
NO 1 : MAC_ADDRESS= 3883.45ef.7984 STATUS= Authorized USER_NAME= admin
VLAN= 2 INTERFACE= gi0/2 USER_TYPE= DOT1X
AUTH_STATE= AUTHENTICATED BACK_STATE= IDLE IP_ADDRESS= 199.0.0.1
IPV6_ADDRESS= Unknown
Online time: 0 week 0 day 0 hours 0 minute 51 seconds
Total: 1 Authorized: 1 Unauthorized/guest/critical: 0/0/0 Unknown: 0
It can be viewed that user PC1 has passed the authentication and then PC1 can visit Update Server and IP Network.
#PC2 can visit Update Server and IP Network without authentication.
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar![Module quang Inphi]() Module quang Inphi
Module quang Inphi![Module Quang Intel]() Module Quang Intel
Module Quang Intel![Module quang Finisar]() Module quang Finisar
Module quang Finisar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng







.png)
























