Network Requirements
- PC1, PC2, and PCs are connected to IP Network via Device.
- PC1 sends the ARP packet to attack Device, Device enables AARF ARP-Guard, Device normally identifies the ARP overspeed, ARP attack, ARP MAC scan, ARP MAC-IP Scan, and the AARF ARP-Guard policy normally takes effect.
Network Topology
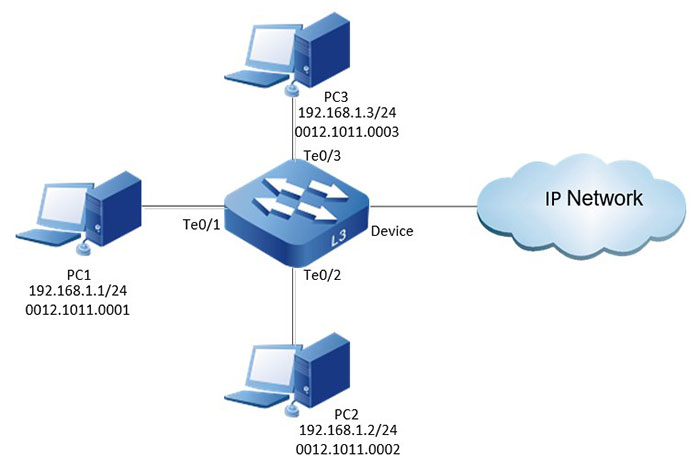
Figure 18–1 Networking for configuring the ARP guard function
Configuration Steps
Step 1: Configure the VLAN and port link type on Device.
#Create VLAN2.
|
Device#configure terminal
Device(config)#vlan 2
Device(config-vlan2)#exit
|
#Configure the link type of port tengigabitethernet0/1, tengigabitethernet0/2, and tengigabitethernet0/3 as Access, permitting the services of VLAN2 to pass.
|
Device(config)#interface tengigabitethernet 0/1-0/3
Device(config-if-range)#switchport mode access
Device(config-if-range)#switchport access vlan 2
|
Step 2: Configure the gateways of PC1, PC2, and PC3 on Device.
#Configure VLAN interface 2 as the gateway of PC1, PC2, and PC3.
|
Device(config)#interface vlan 2
Device(config-if-vlan2)#ip address 192.168.1.254 24
|
Step 3: Enable AARF ARP-Guard on Device.
#Enable AARF ARP-Guard globally.
|
Device(config)#aarf
Device(config-aarf)#arp-guard enable
|
#Enable AARF ARP-Guard on port tengigabitethernet0/1, the related thresholds are the default values, and configure the policy as filter.
|
Device(config-if-tengigabitethernet0/1)# aarf arp-guard enable
Device(config-if-tengigabitethernet0/1)# aarf arp-guard policy filter
|
Step 4: Check the result.
#Query the AARF ARP-Guard configuration information.
Device#show aarf arp-guard configure interface tengigabitethernet 0/1
(Format of column Rate-limit and Attack-threshold is per-src-ip/per-src-mac/per-interface.)
-------------------------------------------------------------------------------------------
Interface/Global Status Rate-limit Attack-threshold Scan-threshold Attack-policy
-------------------------------------------------------------------------------------------
te0/1 Enabled 4/4/100 8/8/200 15 filter
#When the rate of PC1 sending the ARP Request packet for requesting Device Gateway IP address is larger than or equal to the host-based speed limit threshold 4pps and less than the host-based attack threshold 8pps, form the related table entries and output the log information. Device recognizes that the host-based ARP packet is overspeed.
Device#show aarf arp-guard hosts
--------------------------------------------------------------------
Interface Vlan IP MAC Action Policy
--------------------------------------------------------------------
te0/1 2 192.168.1.1 - overspeed monitor
te0/1 2 - 0012.1011.0001 overspeed monitor
Total: 2 record(s).
#The output log is:
Dec 20 2016 03:45:28: %AARF-INTERFACE-3:There are overspeed, attack or scan detected on interface te0/1.(TUE DEC 20 03:45:25 2016)
Dec 20 2016 03:45:28: %AARF-DETECTED-3:Host overspeed was detected.(TUE DEC 20 03:45:25 2016)
Dec 20 2016 03:45:28: %AARF-DETECTED-3:Host overspeed was detected.(TUE DEC 20 03:45:25 2016)
#When the rate of PC1 sending the ARP Request packet for requesting Device Gateway IP address is larger than the host-based attack threshold 8pps, Device filters the ARP packet, forms the related table entries, and outputs the log information. Device identifies the host-based ARP packet attack.
Device#show aarf arp-guard hosts
---------------------------------------------------------------
Interface Vlan IP MAC Action Policy
---------------------------------------------------------------
te0/1 2 192.168.1.1 - attack filter
te0/1 2 - 0012.1011.0001 attack filter
Total: 2 record(s).
#The output log is:
Dec 20 2016 04:30:33: %AARF-INTERFACE-3:There are overspeed, attack or scan detected on interface te0/1.(TUE DEC 20 04:30:30 2016)
Dec 20 2016 04:30:33: %AARF-FILTER-3:Host attack was filter.(TUE DEC 20 04:30:30 2016)
Dec 20 2016 04:30:33: %AARF-FILTER-3:Host attack was filter.(TUE DEC 20 04:30:30 2016)
#When PC1 sends various non-attack ARP Request packets, and the sending rate is larger than or equal to the port-based speed limit threshold 100 and smaller than the port-based attack threshold 200, Device forms the related table entries and outputs the log information. Device identifies the port-based ARP overspeed.
Device#show aarf arp-guard ports
---------------------------------------------
Interface Hosts Scan Action Policy
---------------------------------------------
te0/1 0 0 overspeed monitor
#The output log is:
Dec 22 2016 06:36:32: %AARF-INTERFACE-3:Interface te0/1 was overspeed.(THU DEC 22 06:36:29 2016)
#When PC1 sends various non-attack ARP Request packets, and the sending rate is larger than or equal to the port-based attack threshold 200, Device filters all ARP packets of the port, forms the related table entries and outputs the log information.
Device identifies the port-based ARP attack.
Device#show aarf arp-guard ports
-------------------------------------------
Interface Hosts Scan Action Policy
-------------------------------------------
te0/1 0 0 attack filter
#The output log is:
Dec 22 2016 06:46:58: %AARF-INTERFACE-3:Interface te0/1 was filter.(THU DEC 22 06:46:57 2016)
#When PC1 sends the ARP Request packet with the fixed MAC and increasing Sender IP, and the number of the ARP Request packets sent within 10s exceeds 15, form the related table entries, and output the log information. Device identifies the ARP MAC scanning.
Device#show aarf arp-guard scan
-----------------------------------------------------------
Interface Vlan IP MAC Time-stamp
-----------------------------------------------------------
te0/1 2 N/A 0012.1011.0001 THU DEC 22 03:16:30 2016 Total: 1 record(s).
#The output log is:
Dec 22 2016 03:16:19: %AARF-INTERFACE-3:There are overspeed, attack or scan detected on interface te0/1.(THU DEC 22 03:16:16 2016)
Dec 22 2016 03:16:19: %AARF-SCAN-4:Host scan was detected.(THU DEC 22 03:16:16 2016)
#When PC1 sends the ARP Request packet with the fixed MAC and Sender IP, and the increasing Target IP, and the number of the ARP Request packets sent within 10s exceeds 15, form the related table entries, and output the log information. Device identifies the ARP MAC-IP scanning.
Device#show aarf arp-guard scan
------------------------------------------------------------
Interface Vlan IP MAC Time-stamp
------------------------------------------------------------
te0/1 2 192.168.1.254 0012.1011.0001 THU DEC 22 03:38:52 2016 Total: 1 record(s).
#The output log is:
Dec 22 2016 03:37:33: %AARF-INTERFACE-3:There are overspeed, attack or scan detected on interface te0/1.(THU DEC 22 03:37:30 2016)
Dec 22 2016 03:37:33:%AARF-SCAN-4:Host scan was detected.(THU DEC 22 03:37:30 2016)
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng




.png)
























