Configure a Local Device to Log in to a Remote Device via SSH
Network Requirements
- The local device Device1 acts as the SSH client, while the remote device Device2 acts as the SSH server.
- A route must be available between the two devices.
- The PC can normally log in to Device1.
Network Topology
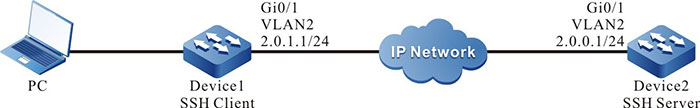
Figure 2‑8 Network Topology for Configuring a Local Device to Log in to a Remote Device via SSH
Configuration Steps
Step 1: Create VLANs, and add ports to the required VLANs.(Omitted)
Step 2: Configures IP addresses for the ports. (Omitted)
Step 3: Configure a local user and the related properties.
#Configure the user name and password of Device2.
|
Device2#configure terminal
Device2(config)#local-user admin1 class manager
Device2(config-user-manager-admin1)#service-type ssh
Device2(config-user-manager-admin1)#password 0 admin1
Device2(config-user-manager-admin1)#exit
|
Step 4: Enable the SSH server function of Device2.
| Device2(config)#ip ssh server |
Step 5: Set the login authentication mode to local authentication.
|
Device2(config)#line vty 0 15
Device2(config-line)#login aaa
Device2(config-line)#exit
|
Step 6: On Device1, log in to Device2 through SSH.
#Configure Device1 to log in to Device2 through SSH.
|
Device1#ssh version 2 2.0.0.1 22 admin1 auth-method 1 admin1
The authenticity of host '2.0.0.1' can't be established
RSA key fingerprint is 7b:ed:cc:81:cf:12:36:6f:f7:ff:29:15:63:75:64:10.
Are you sure you want to continue connecting (yes/no)? yes
Device2>
|
Step 7: Check the result.
If the login succeeds, the shell screen of Device2 is displayed.

-
If the "Connection closed by foreign host" message is displayed, it indicates that the SSH service of the peer end is disabled, or the inputted user name or password is incorrect.
- The SSH server can be configured not to use authentication. If the SSH server does not use authentication, when a client logs in, a user can use any character string as the user name and password.
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng




.png)
























