Configure Intercepting Attack with Same Source and Destination IP Address
Network Requirements
- Device configures the detection function of intercepting the attack with the same source and destination IP address, detecting the attack packet and dropping it.
Network Topology
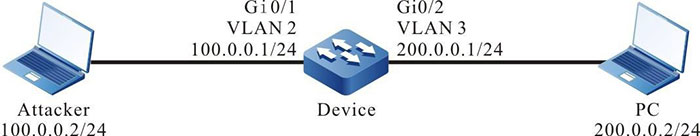
Figure 17–2 Networking of configuring intercepting the attack with the same source and destination IP address
Configuration Steps
Step 1: Configure VLAN and add the port to the corresponding VLAN. (Omitted)
Step 2: Configure the IP address of the interface. (Omitted)
Step 3: Configure the attack detection function.
#Configure the detection function of intercepting the attack with the same source and destination IP address.
|
Device#configure terminal
Device(config)# anti-attack detect src-dst-ip-equal
|
Step 4: Check the result.
#When Attacker initiates the packet attack with the same source and destination IP address to PC, we cannot capture the attack packet on PC.

-
The detection function of intercepting the attack with the same source and destination IP address is valid for the packets processed by CPU and the service packets.
- When the detection function of intercepting the attack with the same source and destination IP address drops the packet, do not generate the log or statistics information.
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng




.png)
























