Network Requirements
- All routers run OSPFv3, and the whole AS is divided to two areas.
- Device1, Device2 and Device3 use the IPSec tunnel to encrypt and authenticate OSPFv3 protocol packets. Device1 and Device2 use ESP transmission and encapsulation mode, the encryption algorithm is 3des, and the authentication algorithm is sha1. Device2 and Device3 use ESP transmission and encapsulation mode, the encryption algorithm is aes128, and the ESP authentication algorithm is sm3.
- After configuration, the device can normally set up the neighbor and learn the routes from each other.
Network Topology
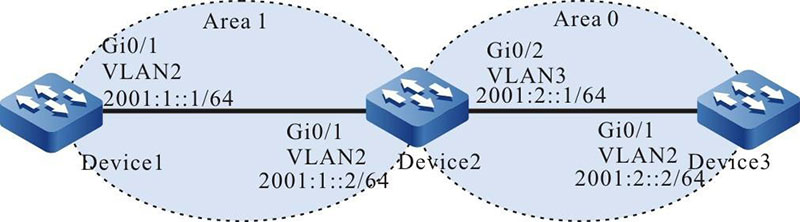
Figure 8-2 Networking for configuring OSPFv3 to use IPSec encrypted authentication
Configuration Steps
Step 1: Configure the IPv6 addresses of the interfaces. (Omitted)
Step 2: Configure an OSPFv3 process, and enable the OSPFv3 function on the corresponding interface.
#Configure the OSPFv3 processes of Device1, Device2, and Device3, and enable OSPFv3 on the interface.
|
Device1#configure terminal
Device1(config)#ipv6 router ospf 100
Device1(config-ospf6)#router-id 1.1.1.1
Device1(config-ospf6)#exit
Device1(config)#interface vlan2
Device1(config-if-vlan2)#ipv6 router ospf 100 area 1
Device1(config-if-vlan2)#exit
Device2#configure terminal
Device2(config)#ipv6 router ospf 100
Device2(config-ospf6)#router-id 2.2.2.2
Device2(config-ospf6)#exit
Device2(config)#interface vlan2
Device2(config-if-vlan2)#ipv6 router ospf 100 area 1
Device2(config-if- vlan2)#exit
Device2(config)#interface vlan3
Device2(config-if- vlan3)#ipv6 router ospf 100 area 0
Device2(config-if- vlan3)#exit
Device3#configure terminal
Device3(config)#ipv6 router ospf 100
Device3(config-ospf6)#router-id 3.3.3.3
Device3(config-ospf6)#exit
Device3(config)#interface vlan2
Device3(config-if-vlan2)#ipv6 router ospf 100 area 0
Device3(config-if-vlan2)#exit
|
Step 3: Configure the IPSec proposal and manual tunnel.
#Configure Device1, create IPSec proposal a, adopt the ESP transmission and encapsulation mode, encrypted algorithm 3des, and authentication algorithm sha1, create IPSec manual tunnel a, and configure SPI and key.
|
Device1(config)#crypto ipsec proposal a
Device1(config-ipsec-prop)#mode transport
Device1(config-ipsec-prop)#esp 3des sha1
Device1(config-ipsec-prop)#exit
Device1(config)#crypto tunnel a manual
Device1(config-manual-tunnel)#set ipsec proposal a
Device1(config-manual-tunnel)#set inbound esp 1000 encryption 0 111111111111111111111111 authentication 0 aaaaaaaaaaaaaaaaaaaa
Device1(config-manual-tunnel)#set outbound esp 1001 encryption 0 aaaaaaaaaaaaaaaaaaaaaaaa authentication 0 11111111111111111111
Device1(config-manual-tunnel)#exit
|
#Configure Device2, create IPSec proposal a, adopt the ESP transmission and encapsulation mode, encrypted algorithm 3des, and authentication algorithm sha1, create IPSec manual tunnel a, and configure SPI and key. Create IPSec proposal b, adopt the ESP transmission mode, encrypted algorthm aes128, and authentication algorithm sm3 ; create Ipsec manual tunnel b, and configure SPI and key.
|
Device2(config)#crypto ipsec proposal a
Device2(config-ipsec-prop)#mode transport
Device2(config-ipsec-prop)#esp 3des sha1
Device2(config-ipsec-prop)#exit
Device2(config)#crypto tunnel a manual
Device2(config-manual-tunnel)#set ipsec proposal a
Device2(config-manual-tunnel)#set inbound esp 1001 encryption 0 aaaaaaaaaaaaaaaaaaaaaaaa authentication 0 11111111111111111111
Device2(config-manual-tunnel)#set outbound esp 1000 encryption 0 111111111111111111111111 authentication 0 aaaaaaaaaaaaaaaaaaaa
Device2(config-manual-tunnel)#exit
Device2(config)#crypto ipsec proposal b
Device2(config-ipsec-prop)#mode transport
Device2(config-ipsec-prop)#esp aes128 sm3
Device2(config-ipsec-prop)#exit
Device2(config)#crypto tunnel b manual
Device2(config-manual-tunnel)#set ipsec proposal b
Device2(config-manual-tunnel)#set inbound esp 2001 encryption 0 1111111111111111 authenti cation 0 aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
Device2(config-manual-tunnel)#set outbound esp 2000 encryption 0 1111111111111111 authent ication 0 11111111111111111111111111111111
Device2(config-manual-tunnel)#exit
|
#Configure Device3, create IPSec proposal b, adopt the ESP transmission and encapsulation mode, encrypted algorithm aes128, and authentication algorithm sm3, create IPSec manual tunnel b, and configure SPI and key.
|
Device3(config)#crypto ipsec proposal b
Device3(config-ipsec-prop)#mode transport
Device3(config-ipsec-prop)#esp aes128 sm3
Device3(config-ipsec-prop)#exit
Device3(config)#crypto tunnel b manual
Device3(config-manual-tunnel)#set ipsec proposal b
Device3(config-manual-tunnel)#set inbound esp 2000 encryption 0 1111111111111111 authenti cation 0 11111111111111111111111111111111
Device3(config-manual-tunnel)#set outbound esp 2001 encryption 0 1111111111111111 authent ication 0 aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
Device3(config-manual-tunnel)#exit
|
Step 4: In the OSPFv3 process, bind the area with the corresponding IPSec tunnel.
#In the OSPFv3 process of Device1, bind area 1 with IPSec tunnel a.
|
Device1(config)#ipv6 router ospf 100
Device1(config-ospf6)#area 1 ipsec-tunnel a
Device1(config-ospf6)#exit
|
#In the OSPFv3 process of Device2, bind area 1 with IPSec tunnel a, and bind area 0 with Ipsec tunnel b.
|
Device2(config)#ipv6 router ospf 100
Device2(config-ospf6)#area 1 ipsec-tunnel a
Device2(config-ospf6)#area 0 ipsec-tunnel b
Device1(config-ospf6)#exit
|
#In the OSPFv3 process of Device3, bind area 0 with IPSec tunnel b.
|
Device3(config)#ipv6 router ospf 100
Device3(config-ospf6)#area 0 ipsec-tunnel b
Device3(config-ospf6)#exit
|
Step 5: Check the result.
#Query the OSPFv3 process information of Device1.
Device1#show ipv6 ospf 100
Routing Process "OSPFv3 (100)" with ID 1.1.1.1
Process bound to VRF default
IETF graceful-restarter support disabled
IETF gr helper support enabled
Initial SPF schedule delay 5000 msecs
Minimum hold time between two consecutive SPFs 10000 msecs
Maximum wait time between two consecutive SPFs 10000 msecs
Minimum LSA interval 5 secs, Minimum LSA arrival 1 secs
Number of external LSA 0. Checksum Sum 0x0000
Number of AS-Scoped Unknown LSA 0
Number of LSA originated 5
Number of LSA received 5
Number of areas in this router is 1
Not Support Demand Circuit lsa number is 0
Autonomy system support flood DoNotAge Lsa
Area 0.0.0.1
Number of interfaces in this area is 1
IPSec Tunnel Name:a , ID: 154
Number of fully adjacent neighbors in this area is 1
Number of fully adjacent sham-link neighbors in this area is 0
Number of fully adjacent virtual neighbors through this area is 0
SPF algorithm executed 4 times
LSA walker due in 00:00:02
Number of LSA 4. Checksum Sum 0x2FC53
Number of Unknown LSA 0
Not Support Demand Circuit lsa number is 0
Indication lsa (by other routers) number is: 0,
area support flood DoNotAge Lsa
You can see that the area is bound with IPSec tunnel a, and the ID is a random value of 0-1023.
#Query the IPSec tunnel information of Device1.
Device1#show crypto tunnel a get the manual tunnel Crypto tunnel a : MANUAL
policy name : (null)
peer address :
local interface : (null) address :
Ipsec proposal : a
Inbound :
esp : spi: 1000 encription key: ******** authentication key: ********
ah spi: 0 authentication key: (null)
Outbound :
esp spi: 1001 encryption key: ******** authentication key: ********
ah spi: 0 authentication key: (null)
route ref : 1
route asyn : 1
route rt_id : 154
You can see that route rt_id is equal to the ID in show ipv6 ospf 100.
#Query the encryption type information of the IPSec tunnel of Device1.
Device1#show crypto ipsec sa tunnel a
route policy:
the pairs of ESP ipsec sa : id :0 , algorithm : 3DES HMAC-SHA1-96
inbound esp ipsec sa : spi : 0x3e8(1000) crypto m_context(s_context) : 0x4cd3ba78 / 0x4cd3bae0
current input 26 packets, 2 kbytes
encapsulation mode : Transport
replay protection : OFF
remaining lifetime (seconds/kbytes) : 0/0
uptime is 0 hour 4 minute 45 second
outbound esp ipsec sa : spi : 0x3e9(1001) crypto m_context(s_context) : 0x4cd3bb48 / 0x4cd3bbb0
current output 39 packets, 3 kbytes
encapsulation mode : Transport
replay protection : OFF
remaining lifetime (seconds/kbytes) : 0/0
uptime is 0 hour 4 minute 45 second
total sa and sa group is 1
You can see that IPSec tunnel a adopts the ESP transmission and encapsulation mode, the encryption algorithm is 3des, and the authentication algorithm is sha1.
#Query the OSPFv3 interface information of Device1.
Device1#show ipv6 ospf interface vlan2 vlan2 is up, line protocol is up
Interface ID 50331913
IPv6 Prefixes
fe80::201:7aff:fecf:fbec/10 (Link-Local Address)
2001 :1::1/64
Interface ID 13
OSPFv3 Process (100), Area 0.0.0.1, Instance ID 0, Enabled 00:41:10, MTU 1500
Router ID 1.1.1.1, Network Type BROADCAST, Cost: 1
IPSec tunnel(Area):a, ID:154
Transmit Delay is 1 sec, State Backup, 3 state change, Priority 1
Designated Router (ID) 2.2.2.2
Interface Address fe80::200:1ff:fe7a:adf0
Backup Designated Router (ID) 1.1.1.1
Interface Address fe80::201:7aff:fecf:fbec
Timer interval configured, Hello 10, Dead 39, Wait 39, Retransmit 5
Hello due in 00:00:06
Neighbor Count is 1, Adjacent neighbor count is 1
Hello received 2 sent 3, DD received 3 sent 4
LS-Req received 1 sent 1, LS-Upd received 5 sent 3
LS-Ack received 3 sent 2, Discarded 0
You can see that the interface is bound with IPSec tunnel a, and the ID is a random value of 0-1023.
#Query the OSPFv3 neighbor information and core route table of Device1.
Device1#show ipv6 ospf neighbor OSPFv3 Process (100)
Neighbor ID Pri State Dead Time Interface Instance ID
2.2.2.2 1 Full/DR 00:00:39 vlan2 0
Device1#show ipv6 route
Codes: C - Connected, L - Local, S - static, R - RIP, B - BGP, i-ISIS
U - Per-user Static route
O - OSPF, OE-OSPF External, M - Management
L ::1/128 [0/0]
via ::, 4d:04:06:36, lo0
C 2001:1::/64 [0/0]
via ::, 03:00:53, vlan2
L 2001:1::1/128 [0/0]
via ::, 03:00:49, lo0
O 2001:2::/64 [110/2]
via fe80::201:7aff:fec9:1cdd, 2d:00:03:49, vlan2
On Device1, the neighbor is set up normally, and the route learning is normal.
#Query the OSPFv3 process information of Device3.
Device3#show ipv6 ospf 100
Routing Process "OSPFv3 (100)" with ID 3.3.3.3
Process bound to VRF default
IETF graceful-restarter support disabled
IETF gr helper support enabled
Initial SPF schedule delay 5000 msecs
Minimum hold time between two consecutive SPFs 10000 msecs
Maximum wait time between two consecutive SPFs 10000 msecs
Minimum LSA interval 5 secs, Minimum LSA arrival 1 secs
Number of external LSA 0. Checksum Sum 0x0000
Number of AS-Scoped Unknown LSA 0
Number of LSA originated 5
Number of LSA received 6
Number of areas in this router is 1
Not Support Demand Circuit lsa number is 0
Autonomy system support flood DoNotAge Lsa
Area BACKBONE(0)
Number of interfaces in this area is 1
IPSec Tunnel Name:b , ID: 2
Number of fully adjacent neighbors in this area is 1
Number of fully adjacent sham-link neighbors in this area is 0
SPF algorithm executed 4 times
LSA walker due in 00:00:02
Number of LSA 4. Checksum Sum 0x24272
Number of Unknown LSA 0
Not Support Demand Circuit lsa number is 0
Indication lsa (by other routers) number is: 0,
area support flood DoNotAge Lsa
You can see that the area is bound with IPSec tunnel b, and the ID is a random value of 0-1023.
#Query the IPSec tunnel information of Device3.
Device3#show crypto tunnel b get the manual tunnel Crypto tunnel b : MANUAL
policy name : (null)
peer address :
local interface : (null) address :
Ipsec proposal : b
Inbound :
esp : spi: 2000 encription key: ******** authentication key: ********
ah spi: 0 authentication key: (null)
Outbound :
esp spi: 2001 encryption key: ******** authentication key: ********
ah spi: 0 authentication key: (null)
route ref : 1
route asyn : 1
route rt_id : 2
You can see that route rt_id is equal to the ID in show ipv6 ospf 100.
#Query the encryption type information of the IPSec tunnel of Device3.
Device3#show crypto ipsec sa tunnel b
route policy:
the pairs of ESP ipsec sa : id : 0, algorithm : AES128 HMAC-SM3
inbound esp ipsec sa : spi : 0x7d0(2000) crypto m_context(s_context) : 0x6a0d9a98 / 0x6a0d9a30
current input 53 packets, 5 kbytes
encapsulation mode : Transport
replay protection : OFF
remaining lifetime (seconds/kbytes) : 0/0
uptime is 0 hour 6 minute 40 second
outbound esp ipsec sa : spi : 0x7d1(2001) crypto m_context(s_context) : 0x6a0d99c8 / 0x6a0d9960
current output 52 packets, 5 kbytes
encapsulation mode : Transport
replay protection : OFF
remaining lifetime (seconds/kbytes) : 0/0
uptime is 0 hour 6 minute 40 second
total sa and sa group is 1
You can see that the IPSec tunnel adopts the ESP transmission and encapsulation mode, the encryption algorithm is aes128, and the authentication algorithm is sm3.
#Query the OSPFv3 interface information of Device3.
Device3#show ipv6 ospf interface vlan2 vlan2 is up, line protocol is up
Interface ID 50331899
IPv6 Prefixes
fe80::200:1ff:fe7a:adf0/10 (Link-Local Address)
2001 :2::1/64
Interface ID 9
OSPFv3 Process (100), Area 0.0.0.1, Instance ID 0, Enabled 00:50:39, MTU 1500
Router ID 3.3.3.3, Network Type BROADCAST, Cost: 1
IPSec tunnel(Area):b, ID:2
Transmit Delay is 1 sec, State DR, 4 state change, Priority 1
Designated Router (ID) 2.2.2.2
Interface Address fe80::200:1ff:fe7a:adf0
Backup Designated Router (ID) 1.1.1.1
Interface Address fe80::201:7aff:fecf:fbec
Timer interval configured, Hello 10, Dead 39, Wait 39, Retransmit 5
Hello due in 00:00:02
Neighbor Count is 1, Adjacent neighbor count is 1
Hello received 272 sent 316, DD received 12 sent 9
LS-Req received 3 sent 5, LS-Upd received 19 sent 18
LS-Ack received 11 sent 13, Discarded 0
You can see that the interface is bound with IPSec tunnel b, and the ID is a random value of 0-1023.
#Query the OSPFv3 neighbor information and core route table of Device3.
Device3#show ipv6 ospf neighbor OSPFv3 Process (100)
Neighbor ID Pri State Dead Time Interface Instance ID
2.2.2.2 1 Full/Backup 00:00:35 vlan2 0
Device3#show ipv6 route
Codes: C - Connected, L - Local, S - static, R - RIP, B - BGP, i-ISIS
U - Per-user Static route
O - OSPF, OE-OSPF External, M – Management
L ::1/128 [0/0]
via ::, 09:53:53, lo0
O 2001:1::/64 [110/2]
via fe80::ae9c:e4ff:fe77:889e, 00:23:36, vlan2
C 2001:2::/64 [0/0]
via ::, 03:05:16, vlan2
L 2001:2::2/128 [0/0]
via ::, 03:05:13, lo0
On Device3, the neighbor is set up normally, and the route learning is normal.
Step 6: On the OSPFv3 interface, bind the corresponding IPSec tunnel.
#Configure Device1, and bind interface vlan2 with IPSec tunnel a.
|
Device1(config)#interface vlan2
Device1(config-if- vlan2)#ipv6 ospf ipsec-tunnel a
Device1(config-if- vlan2)#exit
|
#Configure Device2, and bind interface vlan2 with IPSec tunnel a ; bind interface vlan3 with IPSec tunnel b.
|
Device2(config)#interface vlan2
Device2(config-if- vlan2)#ipv6 ospf ipsec-tunnel a
Device2(config-if- vlan2)#exit
Device2(config)#interface vlan3
Device2(config-if-vlan3)#ipv6 ospf ipsec-tunnel b
Device2(config-if-vlan3)#exit
|
#Configure Device3, and bind interface vlan2 with IPSec tunnel b.
|
Device3(config)#interface vlan2
Device3(config-if- vlan2)#ipv6 ospf ipsec-tunnel b
Device3(config-if- vlan2)#exit
|
Step 7: Check the result.
#Query the OSPFv3 interface information of Device1.
Device1#show ipv6 ospf interface vlan2 vlan2 is up, line protocol is up
Interface ID 50331913
IPv6 Prefixes
fe80::201:7aff:fecf:fbec/10 (Link-Local Address)
2001 :1::1/64
Interface ID 13
OSPFv3 Process (100), Area 0.0.0.1, Instance ID 0, Enabled 00:41:10, MTU 1500
Router ID 1.1.1.1, Network Type BROADCAST, Cost: 1
IPSec tunnel:a, ID:154
Transmit Delay is 1 sec, State Backup, 3 state change, Priority 1
Designated Router (ID) 2.2.2.2
Interface Address fe80::200:1ff:fe7a:adf0
Backup Designated Router (ID) 1.1.1.1
Interface Address fe80::201:7aff:fecf:fbec
Timer interval configured, Hello 10, Dead 39, Wait 39, Retransmit 5
Hello due in 00:00:06
Neighbor Count is 1, Adjacent neighbor count is 1
Hello received 2 sent 3, DD received 3 sent 4
LS-Req received 1 sent 1, LS-Upd received 5 sent 3
LS-Ack received 3 sent 2, Discarded 0
You can see that the interface is bound with IPSec tunnel a, and the ID is a random value of 0-1023.
#Query the OSPFv3 core route table of Device1.
Device1#show ipv6 route
Codes: C - Connected, L - Local, S - static, R - RIP, B - BGP, i-ISIS
U - Per-user Static route
O - OSPF, OE-OSPF External, M - Management
L ::1/128 [0/0]
via ::, 4d:04:06:36, lo0
C 2001:1::/64 [0/0]
via ::, 03:00:53, vlan2
L 2001:1::1/128 [0/0]
via ::, 03:00:49, lo0
O 2001:2::/64 [110/2]
via fe80::201:7aff:fec9:1cdd, 2d:00:03:49, vlan2
On Device1, the route learning is normal.
#Query the OSPFv3 interface information of Device3.
Device3#show ipv6 ospf interface vlan2 vlan2 is up, line protocol is up
Interface ID 50331899
IPv6 Prefixes
fe80::200:1ff:fe7a:adf0/10 (Link-Local Address)
2001 :2::1/64
Interface ID 9
OSPFv3 Process (100), Area 0.0.0.1, Instance ID 0, Enabled 00:50:39, MTU 1500
Router ID 3.3.3.3, Network Type BROADCAST, Cost: 1
IPSec tunnel:b, ID:2
Transmit Delay is 1 sec, State DR, 4 state change, Priority 1
Designated Router (ID) 2.2.2.2
Interface Address fe80::200:1ff:fe7a:adf0
Backup Designated Router (ID) 1.1.1.1
Interface Address fe80::201:7aff:fecf:fbec
Timer interval configured, Hello 10, Dead 39, Wait 39, Retransmit 5
Hello due in 00:00:02
Neighbor Count is 1, Adjacent neighbor count is 1
Hello received 272 sent 316, DD received 12 sent 9
LS-Req received 3 sent 5, LS-Upd received 19 sent 18
LS-Ack received 11 sent 13, Discarded 0
You can see that the interface is bound with IPSec tunnel b, and the ID is a random value of 0-1023.
#Query the OSPFv3 core route table of Device3.
Device3#show ipv6 route
Codes: C - Connected, L - Local, S - static, R - RIP, B - BGP, i-ISIS
U - Per-user Static route
O - OSPF, OE-OSPF External, M – Management
L ::1/128 [0/0]
via ::, 09:53:53, lo0
O 2001:1::/64 [110/2]
via fe80::ae9c:e4ff:fe77:889e, 00:23:36, vlan2
C 2001:2::/64 [0/0]
via ::, 03:05:16, vlan2
L 2001:2::2/128 [0/0]
via ::, 03:05:13, lo0
On Device3, the route learning is normal.

-
When configuring OSPFv3 to bind with the IPSec tunnel, you can only configure the area binding or interface binding, and also can configure the area binding and interface binding at the same time.
- When the area binding and interface binding are configured for the IPSec tunnel at the same interface, the interface binding is prior.
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar![Module quang Inphi]() Module quang Inphi
Module quang Inphi![Module Quang Intel]() Module Quang Intel
Module Quang Intel![Module quang Finisar]() Module quang Finisar
Module quang Finisar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng







.png)
























