Network Requirements
- PC1 and PC2 are connected to IP Network via Device.
- On Device, configure the DAI function of the port, preventing the ARP attack and spoofing.
Network Topology
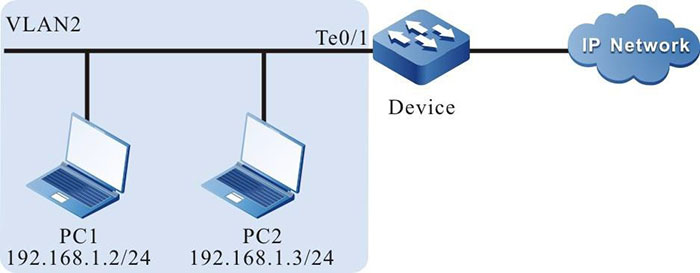
Figure 9-1 Networking of configuring DAI basic functions
Configuration Steps
Step 1: On Device, configure the VLAN and port link type.
#Create VLAN2.
|
Device#configure terminal
Device(config)#vlan 2
Device(config-vlan2)#exit
|
#Configure the link type of port tengigabitethernet0/1 as Access, permitting the services of VLAN2 to pass.
|
Device(config)#interface tengigabitethernet 0/1
Device(config-if-tengigabitethernet0/1)#switchport mode access
Device(config-if-tengigabitethernet0/1)#switchport access vlan 2
Device(config-if-tengigabitethernet0/1)#exit
|
Step 2: Configure the port DAI function on Device.
#Enable port DAI function on port tengigabitethernet0/1, and configure the upper limit of port tengigabitethernet0/1 processing ARP packets as 30pps.
|
Device(config)#interface tengigabitethernet 0/1
Device(config-if-tengigabitethernet0/1)#ip arp inspection
Device(config-if-tengigabitethernet0/1)#ip arp inspection rate-limit 30
Device(config-if-tengigabitethernet0/1)#exit
|
Step 3: On Device, configure the binding entry.
#On port tengigabitethernet0/1, configure MAC address as 0012.0100.0001, IP address as 192.168.1.2, and port IP Source Guard binding entry of VLAN2.
|
Device(config)#interface tengigabitethernet 0/1
Device(config-if-tengigabitethernet0/1)#ip source binding ip-address 192.168.1.2 mac-address 0012.0100.0001 vlan 2
Device(config-if-tengigabitethernet0/1)#exit
|
Step 4: Check the result.
#Query the DAI related configuration information.
Device#show ip arp inspection
Dynamic ARP Inspection information:
Dynamic ARP Inspection log buffer size: 30
Dynamic ARP Inspection log Interval: 20
Dynamic ARP Inspection log Level: 6
Dynamic ARP Inspection interface information :
-----------------------------------------------------
interface status rate-limit(pps) attack
te0/1 enable 30 OFF
te0/2 disable 15 OFF
……
#When the rate of receiving ARP packets by port tengigabitothernet0/1 exceeds 30pps, Device will discard the packets exceeding the rate and output the following prompt message.
Jan 1 02:21:06: The rate on interface tengigabitethernet0/1 too fast ,the arp packet drop!
#When the rate of receiving ARP packets by port tengigabitothernet0/1 exceeds 30pps and lasts for 20 seconds, Device will close port tengigabitothernet0/1 and output the following prompt information.
Jan 1 02:21:26: %LINK-INTERFACE_DOWN-4: interface tengigabitethernet0/1, changed state to down
Jan 1 02:21:26: The rate of arp packet is too fast,dynamic arp inspection shut down the tengigabitethernet0/1 !
#When the ARP packets received by port tengigabitothernet0/1 is inconsistent with the binding entry, Device records the illegal information in the following format to the DAI log and outputs it regularly.
Jan 1 07:19:49: SEC-7-DARPLOG: sender IP address: 192.168.1.3 sender MAC address:0011.0100.0001 target IP address: 0.0.0.0 target MAC address:0000.0000.0000 vlan ID:2 interface ID: tengigabitethernet0/1 record packet :32 packet(s)
#View the DAI log.
Device#show ip arp inspection log-information LogCountInBuffer:1
SEC-7-DARPLOG: sender IP address: 192.168.1.3 sender MAC address:0011.0100.0001 target IP address: 0.0.0.0 target MAC address:0000.0000.0000 vlan ID:2 interface ID: tengigabitethernet0/1 record packet :0 packet(s)
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar![Module quang Inphi]() Module quang Inphi
Module quang Inphi![Module Quang Intel]() Module Quang Intel
Module Quang Intel![Module quang Finisar]() Module quang Finisar
Module quang Finisar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng







.png)
























