802.1X is a broadband access authentication solution put forward by IEEE in June, 2001. It defines the Port-Based Network Access Control. By utilizing LAN’s physical access features of IEEE 802 LAN, 802.1X provides a set of methods for authenticating and authorizing devices access connected to LAN ports via point-to-point.
The 802.1X system is the typical client/server structure, as shown in the following figure, including three entities: Supplicant system (client), Authentication system (authentication device), and Authentication server system (authentication server).
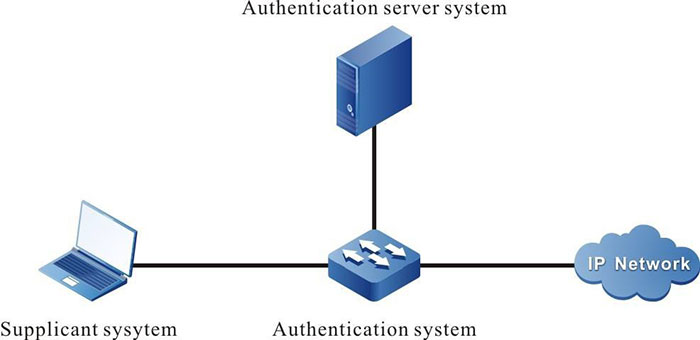
Figure 12-1 802.1X system architecture
- The client installation supports the client software of the 802.1X authentication, sending the authentication request to the authentication device. If authenticating successfully, connect to the network normally.
- The authentication device is between the client and the authentication server, controlling the network access of the client by interacting with the server.
- Usually, the authentication server is the RADIUS (Remote Authentication Dial-In User Service) server, used to verify the validity of the client and inform the authentication result to the authentication device. The authentication device controls the network access of the client according to the authentication result.
EAP (Extensible Authentication Protocol) used by the 802.1X authentication is one general protocol of the PPP authentication, used to interact the authentication information among the client, authentication device and authentication server. The 802.1X protocol uses EAPOL (EAP Over LAN) frame encapsulation format to encapsulate the EAP packet, realizing the interacting between the client and the authentication device. According to the different application scenarios, the 802.1X protocol encapsulates the EAP packet in the different frame formats, realizing the interacting between the authentication device and the authentication server. In the relay authentication mode, the EAP packet is encapsulated in the EAPOR (EAP Over RADIUS) frame format; in the terminating authentication mode, the EAP packet is encapsulated in the standard RADIUS frame format.
The 802.1X authentication mode includes relay authentication mode and terminating authentication mode.
The relay authentication flow is as follows:
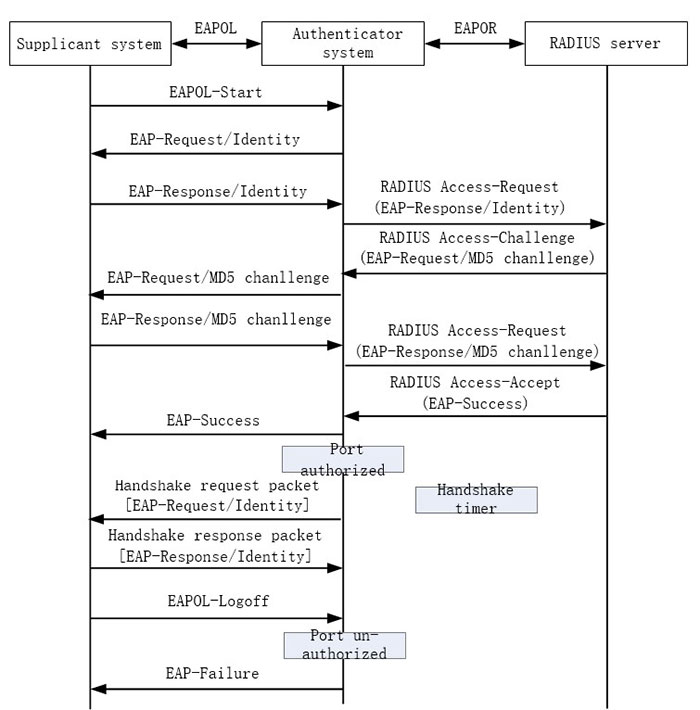
Figure 12–2 802.1X relay authentication flow The relay authentication flow is as follows:
- When the user has the network access requirement, enable the 802.1X client program, input the valid user name and password registered on the authentication server, and initiate the authentication request (EAPOL-Start packet). Here, the client program sends the request authentication packet to the authentication device and starts one authentication process.
- After the authentication device receives the data frame of requesting authentication, send one request frame (EAP-Request/Identity packet) to request the user client program to send the input user name.
- The client program answers the request sent by the authentication device, sending the user name information to the authentication device via the data frame (EAP-Response/Identity packet). The authentication device encapsulates the data frame sent by the client in the packet (RADIUS Access-Request packet) and sends to the authentication server for processing.
- After the RADIUS server receives the user name information forwarded by the authentication device, compare the information with the user name table in the database, find the corresponding information of the user name, and use one randomly-generated encrypting word to encrypt it. Meanwhile, send the encrypted word to the authentication device via the RADIUS Access-Challenge packet; the authentication device forwards it to the client program.
- After the client program receives the encrypted word forwarded by the authentication device (EAP-Request/MD5 Challenge packet), use the encrypted word to encrypt the password (the encryption algorithm is irreversible, generating the EAP-Response/MD5 Challenge packet), and forward to the authentication server via the authentication device.
- RADIUS authentication server compares the received encrypted password information (RADIUS Access-Request packet) with the local encrypted password information. If they are the same, regard the user as valid user and feed back the message of passing the authentication (RADIUS Access-Accept packet and EAP-Success packet);
- After the authentication device receives the message of passing the authentication, change the port to the authorized state, permitting the user to access the network via the port.
- The client also can send the EAPOL-Logoff packet to the authentication device, actively requesting offline. The authentication device changes the port status from authorized to un-authorized, and sends the EAP-Failure packet to the client.
The authentication needs the authentication device and authentication server to support the EAP protocol.
The terminating authentication flow is as follows:
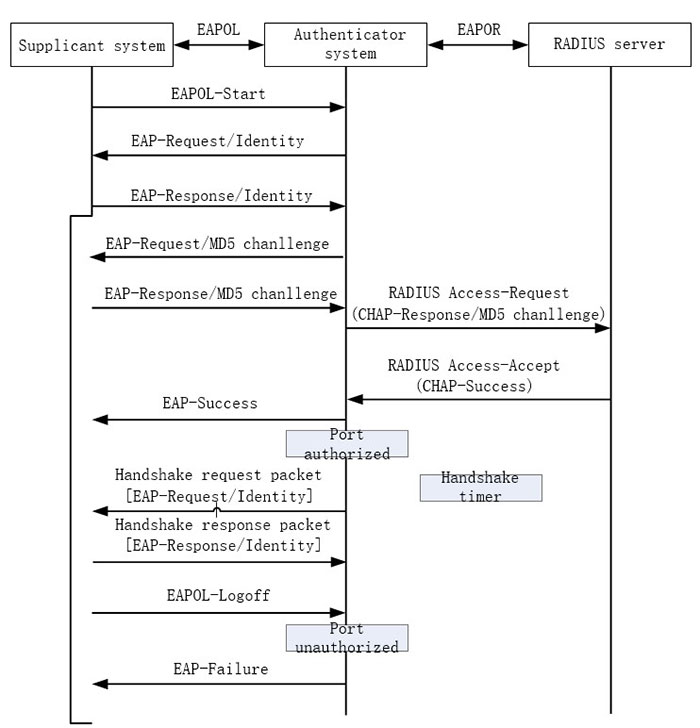
Figure 12-3 802.1X terminating authentication flow
- The difference between the terminating authentication mode and relay authentication mode is: The random encrypting word used to encrypt the user password information is generated by the authentication device. And the authentication device sends the user name, random-encrypting word and password information encrypted by the client to the RADIUS server for authentication.
The terminating authentication mode is used by the authentication server that is deployed earlier and does not support the EAP protocol.
The authentication device supports two access control modes:
- Port-based access control mode (Portbased): After the first user in the port is authenticated successfully, the other access users can access the network without authentication, but after the first user gets offline, the other users also are refused to access the network.
- User-based access control mode (Macbased): All access users in the port need to be authenticated separately. After one user gets offline, only the user cannot access the network and the other users still can access the network.
Auto VLAN is also called Assigned VLAN. When the client passes the server authentication, the server delivers the authorized VLAN information to the authentication device. If the delivered VLAN exists on the authentication device and is valid, the authentication port is added to the delivered VLAN. After the client gets offline, the port is restored to the un-authenticated state, the port is deleted from the Auto VLAN , and the default value of the port is restored to the previous configured VLAN.
After enabling Guest VLAN, the user can and only can access the resources in the VLAN without authentication. After the user is authenticated successfully, the port leaves Guest VLAN, and the user can access other network resources. Usually, the user can get the 802.1X client software in Guest VLAN to upgrade the client, or execute other application program (such as anti-virus software, operation system patch) upgrade. After enabling 802.1x authentication and properly configuring the guest VLAN, the port will be added to the guest VLAN in the untagged mode. At this time, the user under the port in the guest VLAN initiates authentication. If the authentication fails, the port is still in the guest VLAN. If the authentication is successful, it can be divided into the following two cases:
- If the authentication server delivers a VLAN, the port leaves the guest VLAN and joins the distributed VLAN. After the user is offline, the port will return to the guest VLAN;
- If the authentication server does not deliver VLAN, the port leaves the guest VLAN and joins the configured config VLAN in the authentication device. After the user is offline, the port will return to the guest VLAN.
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar![Module quang Inphi]() Module quang Inphi
Module quang Inphi![Module Quang Intel]() Module Quang Intel
Module Quang Intel![Module quang Finisar]() Module quang Finisar
Module quang Finisar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng







.png)


























