Configure Effective Port IP Source Guard Function Based on DHCP Snooping Dynamic Entries
Network Requirements
- PC1 and PC2 are connected to IP Network via Device.
- Configure global IP Snooping function.
- Configure the port IP Source Guard function, so that PC2 can access IP Network normally and PC2 cannot access IP Network.
Network Topology
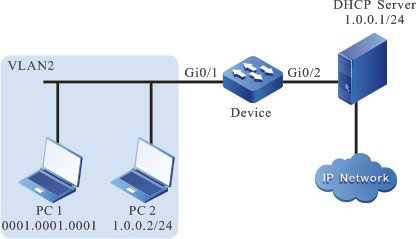
Figure 4–1 Networking of configuring effective port IP Source Guard function based on DHCP Snooping dynamic entries
Configuration Steps
Step 1: On Device, configure VLAN and port link type.
#Create VLAN2.
|
Device#configure terminal
Device(config)#vlan 2
Device(config-vlan2)#exit
|
#Configure the link type of port gigabitethernet0/1 as Access, permitting the services of VLAN2 to pass.
|
Device(config)#interface gigabitethernet 0/1
Device(config-if-gigabitethernet0/1)#switchport mode access
Device(config-if-gigabitethernet0/1)#switchport access vlan 2
Device(config-if-gigabitethernet0/1)#exit
|
Step 2: On Device, enable global DHCP Snooping function and configure gigabitethernet0/2 connected to DHCP Server as the trust port.
|
Device(config)#dhcp snooping enable
Device(config)#interface gigabitethernet 0/2
Device(config-if-gigabitethernet0/2)#dhcp snooping trust
Device(config-if-gigabitethernet0/2)#exit
|
Step 3: Configure the address pool of DHCP Server as 1.0.0.0/24. (omitted)
Step 4: On Device, configure the IP Source Guard function of the port.
#On port gigabitethernet0/1, enable port-based IP Source Guard function.
|
Device(config)#interface gigabitethernet 0/1
Device(config-if-gigabitethernet0/1)#ip verify source
Device(config-if-gigabitethernet0/1)#exit
|
Step 5: Check the result.
#View the configuration information of DHCP Snooping.
Device#show dhcp-snooping
dhcp-snooping configuration information:
dhcp-snooping status:enable
dhcp-snooping option82 information status:disable
dhcp-snooping option82 information policy:replace
dhcp-snooping option82 information format:default
dhcp-snooping option82 information remote id:default(mac address)
dhcp-snooping information relay-address :None
dhcp-snooping binding agent save mode :auto-flash
dhcp-snooping binding agent save delay :1800
dhcp-snooping binding agent save pool :30
dhcp-snooping interface information :
-------------------------------------------------------------------------
interface trust-status rate-limit(pps) circuit-Id
gi0/0/1 untrust 40 default(vlan-mod-interface)
gi0/0/2 trust default(vlan-mod-interface)
gi0/0/3 untrust 40 default(vlan-mod-interface)
gi0/0/4 untrust 40 default(vlan-mod-interface)
gi0/0/5 untrust 40 default(vlan-mod-interface)
……
#View the configuration information of IP Source Guard.
Device#show ip source guard
IP source guard interfaces on slot 0 :
Total number of enabled interfaces : 1
Interface Name Status Verify Type L2 Status
gi0/1 Enabled ip Disabled
gi0/2 Disabled ip Disabled
gi0/3 Disabled ip Disabled
gi0/4 Disabled ip Disabled
gi0/5 Disabled ip Disabled
……
You can see that port gigabitethernet0/1 is enabled with the IP Source Guard function, and Verify Type is ip. Therefore, in the above example, the dynamic entries take effect based on ip+vlan.
#View the IP Source Guard bound entries of the port.
Device#show ip binding table
--------------------------------------------
IP Source Guard binding table on slot 0
Total binding entries : 1
Static binding entries : 0
Dynamic binding entries : 1
Dynamic not write entries : 0
PCE writing entries : 1
-------------------------------------------------------------------------------------
Interface-Name MAC-Address IP-Address VLAN-ID Type-Flag Writing-Flag L2-Flag
-------------------------------------------------------------------------------------
gi0/1 0001.0001.0001 1.0.0.2 2 dynamic Write Not Write
#PC1 can access IP Network normally, and PC2 cannot access IP Network.
 Switch
Switch Wifi - Access Point
Wifi - Access Point Firewall
Firewall Router
Router Module Quang
Module Quang![Module Quang Cisco]() Module Quang Cisco
Module Quang Cisco![Module quang HPE]() Module quang HPE
Module quang HPE![Module quang Maipu]() Module quang Maipu
Module quang Maipu![Module quang Brocade]() Module quang Brocade
Module quang Brocade![Module quang Fortinet]() Module quang Fortinet
Module quang Fortinet![Module quang Aruba]() Module quang Aruba
Module quang Aruba![Module quang OEM]() Module quang OEM
Module quang OEM![Module quang Juniper]() Module quang Juniper
Module quang Juniper![Module quang Dell]() Module quang Dell
Module quang Dell![Module quang Palo Alto]() Module quang Palo Alto
Module quang Palo Alto![Module quang Huawei]() Module quang Huawei
Module quang Huawei![Module quang Arista]() Module quang Arista
Module quang Arista![Module quang F5]() Module quang F5
Module quang F5![Module quang H3C]() Module quang H3C
Module quang H3C![Module Quang Allied Telesis]() Module Quang Allied Telesis
Module Quang Allied Telesis![Module quang SonicWall]() Module quang SonicWall
Module quang SonicWall![Module quang Mikrotik]() Module quang Mikrotik
Module quang Mikrotik![Module quang Handar]() Module quang Handar
Module quang Handar Máy chủ (Server)
Máy chủ (Server) Thiết bị lưu trữ (SAN, NAS)
Thiết bị lưu trữ (SAN, NAS) Load Balancing
Load Balancing Video Conferencing
Video Conferencing Phụ kiện máy chủ
Phụ kiện máy chủ Thiết Bị IoT
Thiết Bị IoT Phụ Kiện Mạng
Phụ Kiện Mạng




.png)
























